
Safe Utilities
Explore integrated utilities technology designed to ensure safety ranging from initial detection to final response across your Mid-Atlantic States energy grid
The Motorola Safety Reimagined Platform for Utilities from Wireless
The Connected Utility
Today, modern utilities are facing ever-increasing demands for reliable, secure service delivery. And the utility business model is fundamentally more complex today than it was even five years ago. Technologies — such as electric vehicles, roof-top solar panels, and smart meters — are becoming more and more prevalent and increasing power consumption. As a result, energy storage is playing an increasingly critical role in balancing load demands. In addition, grid modernization is required to improve the nation’s electrical grid infrastructure to make it more flexible, reliable, resilient, secure and sustainable. On top of this is the ongoing mandate to ensure continuation of service and quick restoration after an outage in order to produce a high level of customer satisfaction. All of this must come together to ensure utilities are able to generate, transmit and deliver energy to customers in an environment built on a foundation of safety and efficiency for employees, visitors, properties, assets and the community.
The Motorola Solutions Safety Reimagined Platform unifies voice, video, data, and analytics technologies on one platform. With Safety Reimagined you can increase security, improve safety, reduce costs, boost efficiency, and improve communications across staff, teams, and locations. These solutions are designed with our customers’ needs at their core; helping Wireless deliver on our promise of creating a safer world.

Safety Reimagined – The Next Generation of Smart Technologies
Improve Safety and Operations on One Platform
Leveraging Motorola’s Safety Reimagined Platform allows your day-to-day operations and emergency situations to be more manageable and measurable for predictable outcomes and optimizations.
Select a use case below and explore
The Safety Reimagined integrated technology ecosystem can provide meaningful outcomes in your power plants and across your energy grid
Propped door / loitering

Propped door alert. Alert sent to security about a door propped open in restricted area outside of a highly secured site.

Loitering alert. Security alerted to group of individuals loitering outside of propped door entrance.

Notification communicated. After initial alerts, image and location of the individuals are sent to field security teams to disperse the crowd and secure the door.

Corrective action taken. Security deters the crowd and takes corrective action. An incident is logged including video feeds for evidence along with other relevant data allowing for further training and analysis.
Field Worker Safety

Alert of escalating customer interaction. A field worker’s customer service call becomes confrontational so the worker activates their body worn camera which sends an alert to the command center or appropriate staff directly on their device of choice.

Real-time video verification. Control room operator determines the location of the distress signal/ worker, via the emergency alert, and views live video stream from their body-worn camera.

Field communication. Control room operator sees the situation is under control but verifies that the worker is now safe over their radio.

Incident documentation. An incident is logged with pre-populated fields and relevant data for analysis and claims.
Temporary Security

Group unrest approaching transformer. Dangerous crowds have been gathering in streets near a high voltage transformer located in a large city. Cameras equipped with video analytics monitoring the fenceline sense motion approaching.

Appearance tracked. Situational awareness maintained as intruder’s appearance is tracked across multiple cameras on and around the transformer.

Resources dispatched. Location and appearance of intruder is determined and shared across security teams to apprehend intruder and deter violence. Security uses microphone to warn intruders they have been detected.

First response dispatched. Local police directly informed with video for immediate response and incident logged with pre-populated fields and relevant data.
Active Assailant

Unusual motion detected at main plant exit. An individual is detected walking against the predetermined directional exit. An alarm is automatically sent to appropriate staff directly on their device of choice and the command center.

Person flagged as armed and dangerous. The security operations center acknowledges the alert and identifies the person as armed moving into the large lobby of the plant.

Resources dispatched. After initial alerts, image and location of the individuals are sent to field security teams to disperse the crowd and secure the door.

Situation resolved. Security has prevented harm, so the incident is logged including video feeds for evidence along with other relevant data allowing for further training and analysis.
Temp Change In Equipment
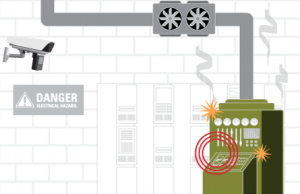
Elevated equipment temperature at remote substation. Thermal cameras detect a temperature change with critical equipment at a remote substation. The alert is sent to the security operations center and to appropriate staff on the device of their choice.
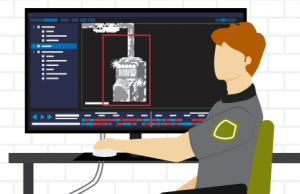
Situational awareness gathered. In the security operations center, nearby cameras are populated to monitor the equipment and the closest response resources are determined using GPS location data.
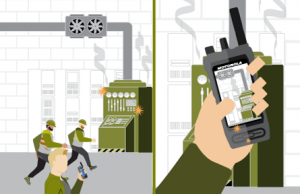
Resources dispatched. Appropriate individuals are dispatched to the area to repair the equipment with an image of the issue, live updates and other multimedia intelligence.
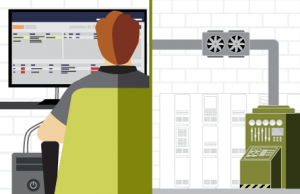
Situation resolved. Technicians arrive to repair the equipment and thermal cameras verify the equipment is properly functioning. An incident is logged with pre-populated fields.
Copper Theft at Substation

Intrusion detected at remote substation. An intruder is detected getting out of a vehicle and jumping the fence of a remote substation. Security is directly notified and live video is transmitted over Private LTE to the control center.

Appearance tracked. Situational awareness maintained as intruder’s appearance is automatically tracked across multiple cameras on and around the substation. Tracking continues even if they appear at another facility.
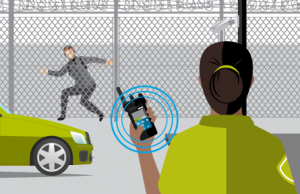
Resources dispatched. Location and appearance of intruder is determined and shared across security teams to apprehend intruder and prevent theft. Security uses microphone to warn intruder they have been detected.

First response dispatched. Local police directly informed with video for immediate response. Incident is logged with pre-populated fields and relevant data to facilitate post investigation and prosecution.
Learn How Safety Reimagined Can Help Your Operations
Safety Reimagined Voice, Video, Data, And Coordination Solutions from Wireless
Improve Safety And Security with a Coordinated Solution
Orchestrate workflow automation tool

